Introduction
In this post we will explore a new command in v7.0.1, tpm report. The purpose of tpm report is to provide easy access to all of the settings that pertain to a specific topic. The default (and only) topic is the security stance. More reports will be added over time.
The Skinny
The Security report reflects the various cluster communications channels. Currently, there are 12 channels reported on:
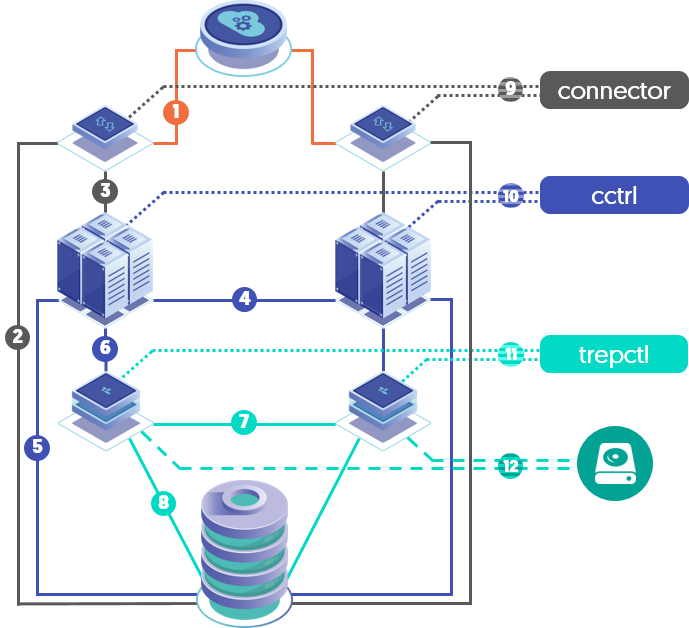
CHANNEL (Protocol)
- Application to Connector (mysql)
- Connector to Database (mysql)
- Connector to Manager (proprietary-routerGateway)
- Manager to Manager (jgroups, rmi/jmx)
- Manager to Database (mysql)
- Manager to Replicator (rmi/jmx)
- Replicator to Replicator (thl)
- Replicator to Database (mysql)
- connector command to Connector (rmi/jmx)
- cctrl command to Manager (rmi/jmx)
- trepctl command to Replicator (rmi/jmx)
- Replicator On Disk (thl encryption)
The Full View
Getting Help
There are not many options for tpm report. The key arguments are --list, --extra, --report, --json and --api:
shell> tpm report -h
The purpose of tpm report is to provide easy access to all of the settings that pertain to a specific topic.
The default (and only) topic is the security stance. More topics will be added over time.
Each topic contains a set of numbered reports. View the list of reports for any topic using --list (or -l)
Limit to reports displayed with --report (or --filter or -r)
Display additional information in the reports with --extra (or -x)
Output as JSON-formatted text with --json
Use the API to gather the data with --api; if API authentication is enabled,
you may need to specify --user and --password if not configured via tpm
Usage: tpm report [args]
>>> Topic Arguments:
--ssl|--security - display current security settings and values (default behavior when no topic is specified)
>>> Option Arguments:
[-l|--list] - list reports by number
[-x|--extra] - provide additional details in the reports
[-r|--report|--filter] - limit display to the specified report number(s); Use a comma-separated numeric list with no spaces to specify multiple reports.
[--json] - Display report as JSON, all other output will be suppressed
[-h|--help]
[-d|--debug]
[-i|--info]
[-q|--quiet]
[-t|--test]
[-v|--verbose]
[--path {fullpath_to_replicator_executables__used_for_thl_and_trepctl}]
[--thl {thl_executable_name_or_fullpath}] (ignores --path)
[--trepctl {trepctl_executable_name_or_fullpath}] (ignores --path)
[--api] Use the v2 API REST interface instead of the command line when possible
[-u|--user {USER}] Specify API auth user (default: not defined)
[-p|--password|--pass {PASSWORD}] Specify API auth password (default: not defined)
If both --user and --password are defined, tpm report will use them.
If either or both --user and --password are missing, tpm report will attempt to derive the values from the configuration.
List All Reports
To display all available reports with ID numbers and descriptions, use --list:
shell> tpm report --list
>>> Security Reports <<<
1. Application to Connector (mysql)
Communications from the client application to the Connector port
2. Connector to Database (mysql)
Communications from the Connector to the Database port
3. Connector to Manager (proprietary (routerGateway))
Communications from the Connector to the Manager
4. Manager to Manager (rmi/jmx, jgroups)
Communications from Manager to Manager
5. Manager to Database (mysql)
Communications from Manager to Database
6. Manager to Replicator (rmi/jmx)
Communications from Manager to Replicator
7. Replicator to Replicator (thl)
Communications from Replicator to Replicator
8. Replicator to Database (mysql)
Communications from Replicator to Database
9. connector Command to the Connector (rmi/jmx)
Communications from the connector cli command to the to local Connector process
10. cctrl Command to the Manager (rmi/jmx)
Communications from the cctrl cli command to the to Manager process
11. trepctl Command to the Replicator (rmi/jmx)
Communications from the trepctl cli command to the to Replicator process
12. Replicator On Disk THL (proprietary (thl encryption))
THL files on disk are encrypted
13. SSL-Specific `tpm` Options for the API (http,https)
Options used by tpm to enable or disable the API for each component
Execute a Specific Report
To display just a single report, specify it using --report {ID#}:
shell> tpm report --report 1
TUNGSTEN SECURITY REPORT as of Thu May 5 20:37:17 UTC 2022
---------------------------------------------------------------------------
>> Comm Channel 1: Application to Connector <<
---------------------------------------------------------------------------
=> CHANNEL INFORMATION:
Connector Bridge Mode: OFF
Application-to-Connector SSL is Enabled
=> TPM OPTIONS:
connector-ssl-capable = true
enable-connector-client-ssl = true
enable-connector-ssl = true
Include Extra Information
To display more information in a report, specify it using --extra (or -x), shown in bold below:
shell> tpm report --extra --report 1
TUNGSTEN SECURITY REPORT as of Thu May 5 20:37:17 UTC 2022
---------------------------------------------------------------------------
>> Comm Channel 1: Application to Connector <<
---------------------------------------------------------------------------
=> CHANNEL INFORMATION:
Connector Bridge Mode: OFF
Application-to-Connector SSL is Enabled (SSL.IN=true, Proxy Mode)
=> TPM OPTIONS:
connector-ssl-capable = true
enable-connector-client-ssl = true
enable-connector-ssl = true
Engage the API
There are two ways to obtain the needed information about the cluster - by calling and interpreting command-line tools or by using the APIv2.
To attempt to gather the information via the API, use --api on the command line. The tpm report command will fall back to the CLI tools if an API method is unavailable for a given report.
shell> tpm report -x --report 1 --api
TUNGSTEN SECURITY REPORT as of Thu May 5 20:43:28 UTC 2022
---------------------------------------------------------------------------
>> Comm Channel 1: Application to Connector <<
---------------------------------------------------------------------------
=> CHANNEL INFORMATION:
APIv2 Connector is SSL Capable: true
APIv2 Connector Requires SSL: true
APIv2 Connector Bridge Mode: false
WARN: No APIv2 solution available for Channel 1: Application to Connector - falling back to CLI
Application-to-Connector SSL is Enabled (SSL.IN=true, Proxy Mode)
=> TPM OPTIONS:
connector-ssl-capable = true
enable-connector-client-ssl = true
enable-connector-ssl = true
Make the Machine Happy
If you wish to output the report in machine-readable JSON-formatted text with other output suppressed, simply add the --json option:
shell> tpm report -x --report 1 --api --json
{
"1" : {
"channelinformation" : [
"APIv2 Connector is SSL Capable: true",
"APIv2 Connector Requires SSL: true",
"APIv2 Connector Bridge Mode: false",
"WARN: No APIv2 solution available for Channel 1: Application to Connector - falling back to CLI",
"Application-to-Connector SSL is Enabled (SSL.IN=true, Proxy Mode)"
],
"metadata" : {
"description" : "Communications from the client application to the Connector port",
"protocol" : "mysql",
"section" : "Application to Connector",
"sslCapable" : 1
},
"tpmoptions" : {
"connector-ssl-capable" : "true",
"enable-connector-client-ssl" : "true",
"enable-connector-ssl" : "true"
}
}
}
List All Reports (Finally!)
To display all reports:
shell> tpm report
shell> tpm report -x
shell> tpm report --json
shell> tpm report -x --json
Wrap-Up
The tpm report command will evolve and grow over time. This first version is Continuent’s way of providing as much transparency about Tungsten Cluster security as possible.

Comments
Add new comment