Introduction
Upgrading a production cluster can be intimidating — especially when transitioning from a non-secure (non-SSL-enabled) to a secure (SSL-enabled) deployment. SSL introduces encryption between all components, improving data integrity and compliance but requiring additional preparation and configuration.
Recently, we helped a customer upgrade both their Tungsten Clustering and a tightly coupled standalone Tungsten Replicator from version 6 (non-SSL) to version 8 (SSL-enabled). The objective was to strengthen data security while maintaining high availability and minimizing downtime.
This post details a proven step-by-step process for handling complex upgrades efficiently, safely, and with little to no service interruption.
Customer Use Case Overview
This upgrade was based on a real-world customer environment running across two geographically separated sites.
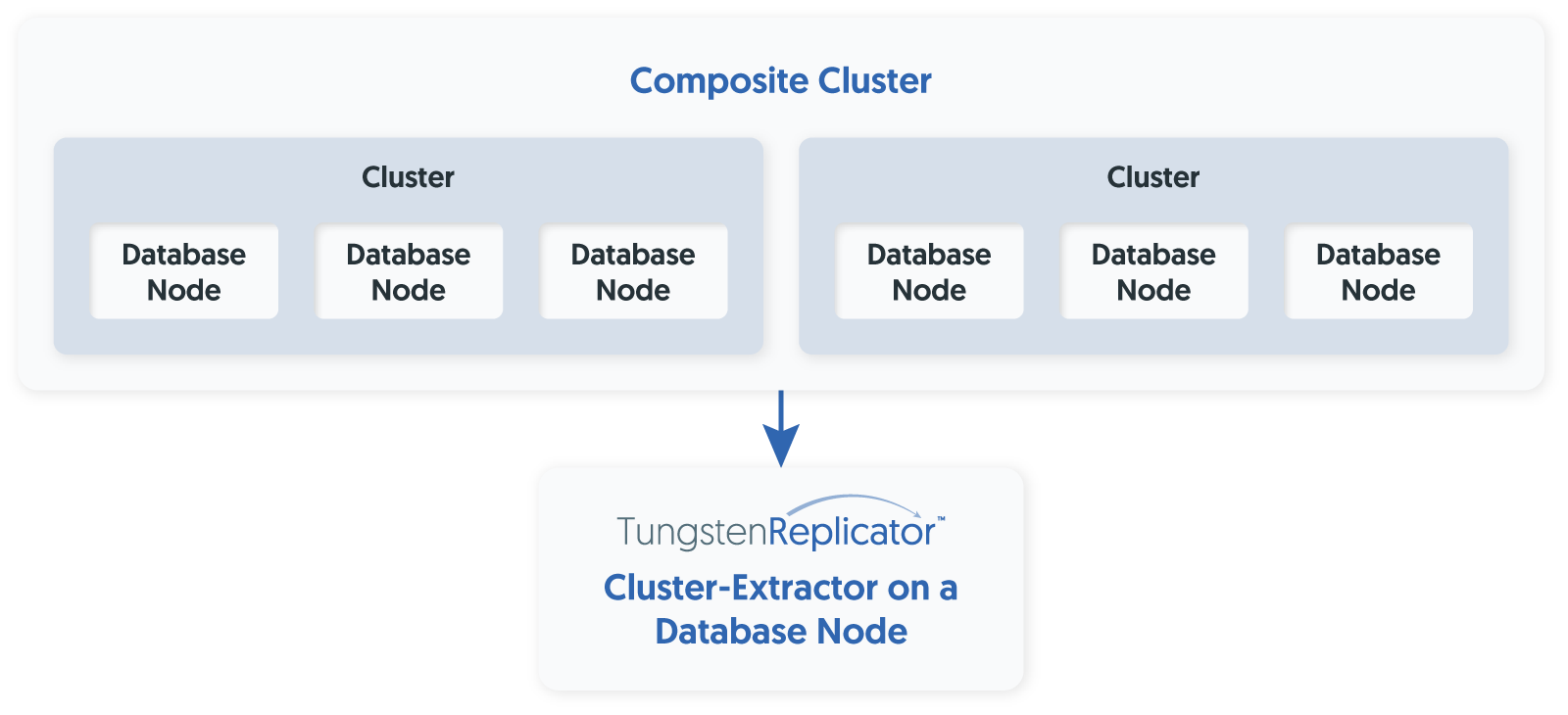
Tungsten Clustering (v6.1.9)
- Topology: Composite Active/Passive
- Sites: 2
- Database Nodes per Site: 3
- Connector Nodes per Site: 2
- SSL: Disabled
Tungsten Replicator (v6.1.9)
- Type: Standalone Cluster-Extractor
- Function: Pulls events from the cluster and applies them to a local MySQL database
- SSL: Disabled
The goal was to upgrade to Tungsten 8.0.x, enabling SSL for all MySQL and Tungsten communication channels.
Pre-Upgrade Preparation
1. Prepare the MySQL Database Nodes
Before upgrading Tungsten, ensure all MySQL database servers are SSL-ready.
-
Generate certificates if none exist:
- ca.pem;
- server-cert.pem;
- server-key.pem;
- client-cert.pem;
- and client-key.pem.
-
Copy the certificates to:
- every database host;
- every Connector node;
- every standalone Replica node.
- Update MySQL configuration to reference these certs.
-
Restart mysqld to apply SSL settings.
# /etc/my.cnf.d/tungsten.cnf [mysqld] ssl-ca=/var/lib/mysql/ca.pem ssl-cert=/var/lib/mysql/server-cert.pem ssl-key=/var/lib/mysql/server-key.pem require_secure_transport=off [client] ssl-ca=/var/lib/mysql/ca.pem ssl-cert=/var/lib/mysql/client-cert.pem ssl-key=/var/lib/mysql/client-key.pemAfter restarting MySQL, verify SSL support:
SHOW VARIABLES LIKE "%ssl%";
2. Prepare the Tungsten Configuration File
Edit /etc/tungsten/tungsten.ini to enable SSL for all MySQL connections, REST APIs, and Connectors.
mysql-allow-intensive-checks=true
disable-security-controls=false
# Enable SSL between Tungsten and MySQL
datasource-enable-ssl=true
datasource-mysql-ssl-ca=/var/lib/mysql/ca.pem
datasource-mysql-ssl-cert=/var/lib/mysql/client-cert.pem
datasource-mysql-ssl-key=/var/lib/mysql/client-key.pem
# Enable SSL for REST API
rest-apis=true
rest-api-address=0.0.0.0
rest-api-ssl=true
rest-api-admin-user=tungsten
rest-api-admin-pass=secret
# Clustering-specific SSL options
enable-connector-ssl=trueFor host prerequisites, see Tungsten Clustering 8.0 Prerequisites
Step-by-Step Upgrade Procedure
Note
Run this procedure on all cluster Database, Connector, and Replica nodes (except where noted).
1. Enable Maintenance Mode
Place the composite service in maintenance mode to avoid failover or automatic transitions during the upgrade.
cctrl -multi
cctrl> use {composite_service}
cctrl> set policy maintenance2. Stop Tungsten Services Gracefully
Stop services on Database and Replica nodes (Connectors can remain online until later).
trepctl -all-services offline
stopall3. Upgrade Tungsten Software
On Database and Replica nodes:
cd /opt/continuent/software/tungsten-clustering-8.0.1-183
./tools/tpm update --replace-release --add-sslOn Connector nodes:
cd /opt/continuent/software/tungsten-clustering-8.0.1-183
./tools/tpm update --replace-release --add-ssl --no-connectors4. Distribute Tungsten Certificates
After upgrading one Database node, propagate the Tungsten-generated certificates to all other nodes.
tpm copy --initFor standalone Replica hosts:
scp /opt/continuent/share/[jpt]* ${replica_host}:/opt/continuent/share
scp /opt/continuent/share/.[jpt]* ${replica_host}:/opt/continuent/shareEnsure correct ownership and permissions:
chown -R tungsten:tungsten /opt/continuent/share
chmod 600 /opt/continuent/share/*.pem5. Restart and Validate Tungsten Services
Bring services back online:
startall
trepctl online
trepctl -all-services statusConfirm replication status shows all services ONLINE, and verify SSL connectivity.
6. Promote and Restart Connectors
Gracefully promote and restart Connectors to apply the new version and SSL configuration.
cd /opt/continuent/software/tungsten-clustering-8.0.1-183
./tools/tpm promote-connector
tpm connectorTo verify MySQL connections are now encrypted:
mysql> \sLook for SSL: Cipher in use is...
7. Restore Automatic Mode
Once all nodes are validated, restore automatic operation.
cctrl
cctrl> use {composite_service}
cctrl> set policy automaticPost-Upgrade Validation
- Confirm that Connectors are using SSL by checking connection status (\s).
- Ensure that all Replication services show ONLINE.
- Verify REST API access via HTTPS.
- Review Tungsten logs for SSL handshake or connection errors.
Conclusion
Transitioning from a non-SSL to SSL-enabled Tungsten environment is a critical step toward enhanced data security and compliance.
With careful preparation — ensuring MySQL SSL readiness, updating Tungsten configurations, and properly distributing certificates — the process can be executed smoothly and with little to no downtime.
In this customer deployment, the entire upgrade process — from preparation through validation — was completed efficiently and securely, demonstrating the robustness of the Tungsten 8.0 platform in managing complex high-availability environments.
Key Takeaways
- Always validate MySQL SSL before upgrading Tungsten.
- Run upgrades in maintenance mode for safety.
-
Use
tpm copy --initto synchronize certificates across nodes. - Perform Connector promotion to gracefully roll forward client access.
- Finalize with automatic mode to restore HA policies.

Comments
Add new comment